Cyber Crime Trend – On the rise
Data Sources – IT Governance Co. UK, FBI, RSA Labs, NCSC UK.
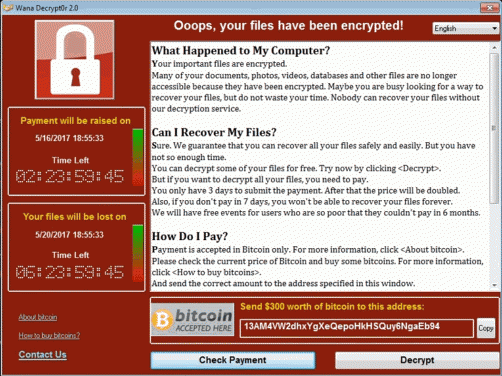
Ransomware is currently undergoing a rapid rate of growth. For an explanation of ransomware refer to https://www.ncsc.gov.uk/guidance/protecting-your-organisation-ransomware
Ransomware is only one of many different types of criminal threats and risks for your computer systems.
Ransomware Do’s and Don’ts
Always:
- Follow the “prevention” steps listed below and follow the recommended checklist
- If you notice any unusual activity contact Communicat immediately.
- Shut down your computer systems as quickly as possible and do not re-start them until after you have spoken to Communicat.
Never:
- Never pay the criminals. Why would you trust criminals who are already blackmailing you? If you pay the criminals then they will only place you on a “hotlist” or organisations that they can attack again and again in the future.
Overview of Ransomware and Malware Strategy
The number and sophistication of attacks by computer criminals is increasing dramatically, requiring businesses to conduct regular reviews of security protection methods. In short, the security measures that you had in place last year may no longer be adequate. This is one reason why most organisations engage Managed Services IT specialists to provide a complete security umbrella to protect against criminal activity.
Details of the different types of threats are too numerous to mention here. Broad categories of threats include Ransomware, Trojan, Keylogger, Virus, Worm, Spyware, Scareware, Adware, Backdoor, Exploit, Botnet, Phishing, Cookies, etc.
The type and sophistication of threats is constantly increasing and evolving, therefore necessitating new solutions to invented by computer support organisations such as Communicat, who offer security protection.
To protect your computer system you need a multi-layered system and strategy, which basically comprises two main components. Prevention is always preferred, in order to avoid disruption to your business. The aim of prevention is to reduce the probability of disruption to a minimum, however risks cannot be entirely eliminated. For example, there is a constant race between criminals and solution providers, therefore resulting in “zero day vulnerability”, where criminals commence a new malware activity and there is a delay while solution providers develop a remedy.
If prevention is not successful, then the fallback is to ensure that you have an effective recovery system that can provide reinstatement of your data and your computer systems.
Prevention
- User education e.g. ensuring that users adopt complex and secure passwords, and recognise suspicious behaviour (e.g. a bogus email);
- Hotline support so that users can immediately call for advice if there is any suspicious activity;
- Constant online monitoring of system using Managed Services systems provided by IT companies such as Communicat. Managed Services involves software that is aware of the latest threats and which constantly watch your computer systems to detect any problems, and to take corrective action;
- Malware protection including constant updates of anti-virus, anti-malware;
- Checking security settings on your browser;
- Regular upgrades of your computer’s operating system and software;
- Firewall security;
- Network security must be set up to isolate different components of your computer systems to reduce the chance of cross-infection;
- Spam protection – there are different levels of Spam protection available at different costs. Choose the level that is best suited to your risk prevention requirement.
Recovery
If you suffer loss of data then some level of disruption to your business will be inevitable. It is important to have a sound backup strategy so that disruption is minimised.
It will be essential that you are able to restore your system from a recent backup.
- Reliable, regular, automated and entire system backups of your entire computer system are essential.
- Backups must be stored off-site and in a secure location. Online cloud backups are one way to achieve this.
- Backups must be protected by network configuration so that backups are completely separate from your main network, in order to protect against cross-infection.
- Backups must be checked on a regular basis by trained professions.
- For businesses there should always be a double backup solution, so as to ensure that backups are processed quickly and completely on the local site and then updated to the off-site location. This will ensure that full and complete backups are achieved every day, without being restricted by working hour limitations.
Multi-Layered Levels of Protection
This simplified explanation is intended to explain the reasons why a multi-layered protection strategy is required.
Remember that your computer security is only as strong as your weakest link. One small “hole” in your computer security strategy will leave you vulnerable to criminals who can exploit such an opportunity.
It is impossible to make your computer system 100% secure, just as it is impossible to make your home or your vehicle completely secure against criminal activity. Therefore, the practical strategy is to find the right balance between the cost of protection and the level of security required.
The achievement of computer security requires professional assistance and computer systems that are out of reach to any computer user, small/medium business or small IT company. Make sure your computer security consultants are equipped with the latest technology and skilled personnel.
Backups
Many organisations find out the hard way that their backup procedures are not as effective as they had believed.
Risks include:
- Your backups may be infected with the same Malware as your mainstream system, therefore rendering your backups useless. Security configuration is required to ensure that your backup systems are completely isolated from being affected by problems (e.g. ransomware) affecting your main computer system;
- Are your backups really working? Unfortunately, backup technology can be subject to failure. Your system may be reporting that your backups are working correctly, but how to you really know they are working properly? The only way to find out if your backups are working correctly is to restore your data to a live system and then observe if the restore is completely successful. This is an expensive and time-consuming process;
- Is your entire system being backed up? Some organisations discover that they are only backing up part of their system, e.g. their data. Therefore, if there is a major system failure, they cannot re-instate the complete system to operational status.
- Are your backups managed by a proven backup cycle – grandfather, father, son, etc. In other words, are you able to roll back your data to yesterday, last week, last month, etc. This will be important if your main backup is not able to be accessed, e.g. it has been affected by ransomware encryption. In that case you will need to revert to an older backup.
Umbrella Protection for your Computer System
Communicat can partner with you as your IT partner. We can provide you with a full umbrella of support. We have invested in the best technology, training and skilled personnel to provide you with the level of protection you need.
